In the following post I will demonstrate a VPN site-to-site
(L2L) configuration between Cisco ASA and Fortigate appliances.
These are the customer demands for the following setup:
- VPN site-to-site between Office 1 and Office 2
- All traffic from Office 2 should pass-through office 1
- When Office 2 goes to the internet they will using Office 1
external IP
This is my lab setup:
Let’s start with the Fortigate configuration,
VPN -> IPsec ->Tunnels
Type in a name for this tunnel and select Custom VPN Tunnel
(No Template)
Fill in the required information, type in the remote IP
address (10.1.0.1), fill in the pre-shared key and select phase 1 proposal, here
I choose IKEv1 with AES192 and SHA1 using DH group 2 (1024bit) and key lifetime
of 86400 seconds (24 hours).
Continue filling phase 2 selectors, type in the local
networks, in this case I summarize Office 2 networks to 192.168.48.0/21, and
remote networks which in my case should be 0.0.0.0/0.0.0.0 in order to route
all traffic through the VPN tunnel, and phase 2 proposal - here I choose again
AES192 with SHA1 and DH group 2, also check PFS and type in the key lifetime to
86400 seconds.
Note that I removed all other options in phase 1 and 2
proposals and leave only AES192 with SHA1.
Now go to Policy & Objects -> Objects -> Addresses
and create new address for remote network:
And another one for the local networks:
Now let’s configure the firewall policy, go to Policy &
Objects -> Policy -> IPv4 and create new policy, from interface NET50
(VLAN50) with source address LOCAL_NETWORK to interface OFFICE1 (VPN interface)
with destination address REMOTE_NETWORK and without NAT:
Crate another policy in the opposite way:
For each network we would have to do these policies (VLAN
50, VLAN51 and so on), also this is the place for limit the access between the
two sites (for example create policy which allows only HTTP and HTTPS between the
two).
Last we need to configure static route toward the VPN
tunnel, go to Router -> Static -> Static Routes and create new static
route, type 0.0.0.0/0.0.0.0 for destination and choose OFFICE1 (VPN interface)
as Device:
Note that we will also need static route to remote device
(Cisco ASA at 10.1.0.1) with ISP next-hop:
Now let’s configure the Cisco ASA, here I will use the built-in
wizard for creating the tunnel but I’ll explain on each part of the
configuration and will show also CLI configuration.
First we need to configure object for the remote network, Open
the ASDM and go to Configuration -> Firewall -> Objects -> Network
Objects/Groups, click on Add and create an object for the remote network:
And another object fot the local network:
Again here I summarize for all OFFICE1 networks
(192.168.0.0/21).
Now click on Wizards from the tool bar, choose VPN Wizards
-> Site-tosite VPN Wizard…
On the first screen click Next
Type in the Fortigate external IP (10.2.0.1) and choose the
Cisco ASA external interface (EXTERNAL1):
Click Next
On the Local Network choose Any4 and on the Remote Network
choose the object we have just created (REMOTE_NETWORK):
Click Next
Choose Customize Configuration and type in the pre-shared
key in all 3 places (although we are not going to use IKEv2 it’s necessary in
order to be able to move between the tabs)
Click on IKE Version tab and clear IKEv2 checkbox
Click on Encryption Algorithms tab and then click on IPsec
proposal Select button
Clear all settings under Assign-> and choose only
ESP-AES-192-SHA (Tunnel mode), then click OK
Click on Perfect Forward Secrecy and mark the checkbox to
enable it:
On the NAT exempt screen click Next
On the Summary screen review the settings and click Finish
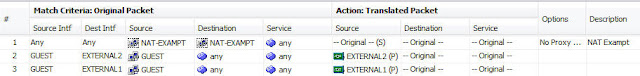
Now we need to create NAT policy which will exempt the traffic
between OFFICE1 and OFFICE2 networks, go to Configuration -> Firewall ->
NAT Rules and click add:
Create NAT policy for keeping the original IP from remote to
local and vice versa:
This rule is bi-directional so we won’t need to configure
the opposite.
Now we need to configure firewall access rule for the VPN
traffic, go to Configuration -> Firewall -> Access Rules and click Add:
Create access rule on the external interface (EXTERNAL1)
with REMOTE_NETWORK (192.168.48.0/21) as source and any as destination:
Of course this rule should be above implicit deny rule if
configured.
Click save and then apply.
That’s it – the tunnel should be up and running.
Now let’s review on the wizard configuration, go to
Configuration -> Site-to-Site VPN and choose Connection Profiles, here we
should see the connection profile for the newly created tunnel:
Here we can see the protected networks, the group policy, pre-shared
key and phase1/phase2 encryption algorithms.
On the Crypto Map Entry we can see some more settings such
as NAT-T and Reverse Route Injection:
And on the Tunnel group we can see the IKE keepalive
settings:
Under Configuration -> Site-to-Site VPN -> Group
Policies we can find the tunnel created policy which allow us to choose
tunneling protocol and different timers (idle, maximum connect time) and also
Filter option which gives us the ability to create and configure ACL for
permit/deny traffic on this tunnel.
Under Configuration -> Site-to-Site VPN -> Advanced
-> Crypto Maps we can find the tunnel map where we have some more settings
such traffic selection:
Next post i will provide the CLI configuration, NAT for VPN traffic and some debugging commands.