Network Topology:
Requirements: ASA image version 9.4 or higher
First step is to configure an ACL go to Firewall->Advanced->ACL
Manager and click Add
The purpose of this ACL is to catch the
required traffic for match, here in my example I’ll use the guest network
(192.168.7.0/24).
The ACL name is ACL_GUEST_PBR, where the first
ACE is to deny internal traffic to be match, Here I deny the guset network to the dev
network (192.168.2.0/24):
Then add permit ACE which match guest network
to all destinations:
Then go to Device Setup->Routing->Route
Maps and click Add to create the route-map, RM_GUEST_PBR.
In the Match Clause tab we will configure the
match criteria, in my example the ACL_GUEST_PBR along with route-map name and sequence
number:
Go to Policy Based Routing tab, You may get the IP Address Mismatch warning, just click yes and ignore it:
click on Set default
next-hop IP address and enter the next hop IP:
Click OK
Next go to Interface Settings->Interfaces,
choose the source interface, in my example the Guest interface Gi0/1.7
Click edit and under Route Map choose the PBR
route map RM_GUEST_PBR:
Click OK
Don’t forget to configure Firewall access rules
and NAT rules as needed.
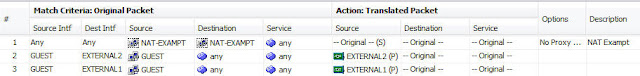
Here in my example I’ve configured two NAT
rules, one for each link:
In order to debug policy-based route use the
following command:
|
debug policy-route
|
Here is an example of successful PBR, where my
client (192.168.7.31) tries to ping outside IP (172.16.0.30):
|
pbr: policy based route
lookup called for 192.168.7.3/1 to 172.16.0.30/0 proto 1 sub_proto 8 received
on interface GUEST
pbr: First matching rule from
ACL(20)
pbr: route map RM_GUEST_PBR,
sequence 10, permit; proceed with policy routing
pbr: 'default' option
configured; lookup for an explicit route to 172.16.0.30
pbr: no explicit route to 172.16.0.30
found
pbr: evaluating default
next-hop 2.2.2.2
pbr: policy based routing
applied; egress_ifc = EXTERNAL2 : next_hop = 2.2.2.2
|
And an example of denied match on PBR, where my
client tries to ping internal address (192.168.2.254):
|
pbr: policy based route
lookup called for 192.168.7.3/1 to 192.168.2.254/0 proto 1 sub_proto 8
received on interface GUEST
pbr: First matching rule from
ACL(20)
pbr: found route policy with
a matching deny ACL; Check next matching rule.
pbr: no route policy found;
skip to normal route lookup
|







grt
ReplyDelete