First generate CSR (Certificate Signing Request), from the
security gateway, to sign it on a valid certificate authority - CA, like
GoDaddy, Thawte, Versign etc.
Run this command on the security gateway (that runs also the
mobile access):
|
cpopenssl req
-new -newkey rsa:2048 -out CERT.CSR -keyout KEYFILE.KEY -config
$CPDIR/conf/openssl.cnf
|
A run output example:
|
[Expert@CP-SG1:0]# cpopenssl
req -new -newkey rsa:2048 -out CERT.CSR -keyout KEYFILE.KEY -config
$CPDIR/conf/openssl.cnf
Generating a 2048 bit RSA
private key
.........................................+++
............................................................................................................................................................+++
writing new private key to
'KEYFILE.KEY'
Enter PEM pass phrase:
Verifying - Enter PEM pass
phrase:
-----
You are about to be asked to
enter information that will be incorporated
into your certificate
request.
What you are about to enter
is what is called a Distinguished Name or a DN.
There are quite a few fields
but you can leave some blank
For some fields there will be
a default value,
If you enter '.', the field
will be left blank.
-----
Country Name (2 letter code)
[AU]:IL
State or Province Name (full
name) [Some-State]:TLV
Locality Name (eg, city) []:TLV
Organization Name (eg,
company) [Internet Widgits Pty Ltd]:COMPANY
Organizational Unit Name (eg,
section) []:IT
Common Name (eg, your name or
your server's hostname) []:ssl.company.com
Email Address []:administrator@company.com
Please enter the following
'extra' attributes
to be sent with your
certificate request
A challenge password []:
An optional company name []:
[Expert@CP-SG1:0]# ls
CERT.CSR KEYFILE.KEY
[Expert@CP-SG1:0]#
|
Note that most of the details (marked in green) are just for
formality and proper information in the certificate, most important fields are
the common name, which must be the site DNS name and the e-mail, which most CA
will send the certificate to (it must be admin@ or adminsitartor@ account).
In the end of the process we will get two files:
CERT.CSR is the certificate signing request that we will
send to the CA for signing.
KEYFILE.KEY is the file which holds the private key for the
certificate, Save this file in very secure place, also write down the password
for this file (in secure place) – we will need it later on.
Now all you have to do is to send CERT.CSR file to the CA
for signing and wait for an e-mail (in administrator@company.com mailbox)
with the signed certificate.
This is PEM certificate example received from the CA:
|
-----BEGIN
CERTIFICHTE-----
MIIEfDCCH9SgHwIBHgIQHPuD9eDiE0VwdreDnFmubjHNBgkqhkiG9w0BHQsFHDBj
MQswCQYDVQQGEwJVUDEVMBMGH8UEChMMdGhhd3RlLCBJbmMuMR0wGwYDVQQLExRE
b98hHW4gVmFsHWRhdGVkIFNTTDEeMBwGH8UEHxMVdGhhd3RlIERWIFNTTCBDQSHt
IEcyMB4XDTE8MDkwNjHwMDHwMFoXDTE3MDkwNTIDNTk8OVowGDEDMBcGH8UEHxQQ
c3NsLmdhbGF0ei5jby5pbDCCHSIwDQYJKoDIhvcNHQEBBQHDggEPHDCCHQoCggEB
HOHsIfVypDyOhvr6yXxuQNmk6Lnf3uvYJv8xYgcfCMYs0EYpQf5o9p8DVcy7oc/W
YJ+gxDTeykDWGvfih/NdrHceyWXtVDDxQDcgfKmHoncHJktmLnQDPCF4EC+k3pkP
x5DnQt/rK6djxMBkRwN7S8PVCDi788OeGpebbqpYX+le9ciOG650SjHV8yf6bYGD
Kk58d88eQYn9cEXEuTef6SyIhNDsU5fPxd9MTDsHdHHRoireQk3swES4UDKD4jVp
Le/Jjw3KfPinJyhsQcJJ9ESWTv/HQ/9igLvPyv7lF883PGUW8qE6qNg5DBfvOwvf
UIhoBVSt9S/fNeuGIhJMmk0CHwEHHHOCHXIwggFuMBsGH8UdEQQUMBKCEHNDbC5n
YWxhdHouY98uHWwwCQYDVR0TBHIwHDHrBgNVHR8EJDHiMCCgHqHchhpodHRwOi8v
dG4uc3ltY9IuY99tL3RuLmNybDBuBgNVHSHEDDBlMGMGBmeBDHECHTBDMCYGCCsG
HQUFBwIBFhpodHRwcDovL3d3dy50HGF3dGUuY99tL9NwcDHvBggrBgEFBQcCHjHj
DCFodHRwcDovL3d3dy50HGF3dGUuY99tL3JlcG9DHXRvcnkwHwYDVR0jBBgwFoHU
n7jBqWDy9cHiKpTtXJms8ODXxgcwDgYDVR0PHQH/BHQDHgWgMB0GH8UdJQQWMBQG
CCsGHQUFBwMBBggrBgEFBQcDHjBXBggrBgEFBQcBHQRLMEkwHwYIKwYBBQUHMHGG
E9h0dHH6Ly90bi5DeW8jDC5jb90wJgYIKwYBBQUHMHKGGmh0dHH6Ly90bi5DeW8j
Yi5jb90vdG4uY3J0MH0GCSqGSIb3DQEBCwUHH4IBHQCxDHU+tDieQ+rKDuFCm3or
cHYRHSe8g/eIqyN+xwy/V+lb4CipYYtwNH/wN9jL9uLjf/BCBjjEPFn9IDeDIBDl
yK99PNjUxlh50Ik0lY+8NBwFwT86YrLi8HKHyStFbXLyNLD8Mf9o8GbueuKcHD57
cjocpYoQPDxK9KKhY8nDDkXv69CMQcvS9DgkTj6HgDDV6vNOFo0e3GvXMlFpfdOE
rNYtvQ8O7E8lvl8v7QS8uTDYd70eTCX7Unk4/ONJOKl9HVGi97q9VTYOKUFNwB7W
uHP+Chqf8ppmDylGebD8cHukfv7+9BijpUDc+PNlb9/5xYsO8RCS3UhMIMd7wmDH
-----END
CERTIFICHTE-----
|
Now we need to convert the PEM to .p12 format, create text
file and copy the certificate into it,
Copy the text file (I called it CA_CERTIFICATE.TXT) and both
CERT.CSR and KEYFILE.KEY, to the security gateway – here in this example I have
created a new directory under /home directory called CERT:
|
[Expert@CP-SG1:0]#
ls -la
total 16
drwxrwx--- 2
admin root 4096 Sep 8 12:54 .
drwx------ 3
admin root 4096 Sep 8 12:54 ..
-rw-rw---- 1
admin root 1054 Sep 8 12:40 CERT.CSR
-rw-rw---- 1
admin root 0 Sep 8 12:54 CA_CERTFICATE.TXT
-rw-rw---- 1
admin root 1743 Sep 8 12:40
KEYFILE.KEY
|
Now run the following command:
|
cpopenssl
pkcs12 -export -in CA_CERTIFICATE.TXT -inkey KEYFILE.key -certfile CERT.CSR
-out SSL_CERTIFICATE.p12
|
Enter the private key password, and type new export password
(which will be required in case of exporting the password).
Now enter the SmartDashboard, double click on the relevant security
gateway under network objects, and select Mobile Access -> Portal Settings,
click on Replace… key:
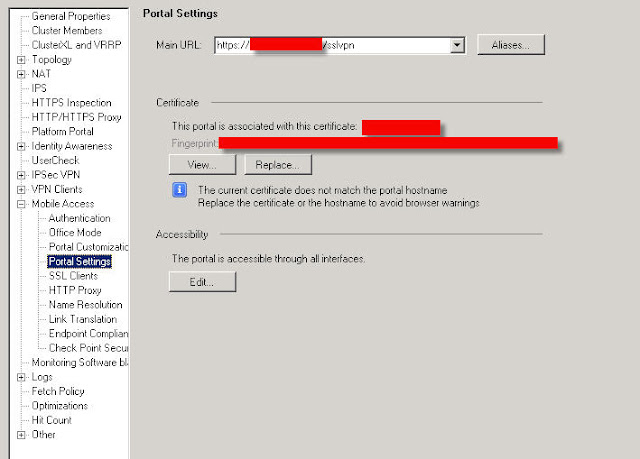
Choose the newly created file named: CERTIFICATE.p12
Close this window and install policy.






