This post I will show how to configure Juniper
SRX (650) in cluster for HA mode.
In this scenario there are two ISP’s, where I need
to peer with each other using BGP.
This is the network topology:
First remove any interface or configuration from
the device:
|
root@%
cli
root>
configure
Entering
configuration mode
[edit]
root#
delete
This
will delete the entire configuration
Delete
everything under this level? [yes,no] (no) yes
[edit]
root#
set system root-authentication plain-text-password
New
password:
Retype
new password:
[edit]
root#
commit
commit
complete
root#
run show configuration
##
Last commit: 2015-10-20 01:14:22 UTC by root
version
12.1X44-D35.5;
system
{
root-authentication {
encrypted-password "fVsds%xw#7NYGHN3VFDS#|EGH6bjuS";
## SECRET-DATA
}
}
[edit]
|
Control link:
On the SRX650 device, connect ge-0/0/1 on device
A to ge-0/0/1 on device B.
The ge-0/0/1 interface on device B will change
to ge-9/0/1 after clustering is enabled in step 2. Note: It is strongly
recommended that the interfaces used for the control link are connected directly
with a cable (instead of a switch).
Fabric (Data) link:
On the SRX650 device, connect ge-0/0/2 on device
A to ge-0/0/2 on device B.
The ge-0/0/2 interface on device B will change
to ge-9/0/2 after clustering is enabled in step 2.
Step 1 - enable chassis cluster:
Note that this is done in the operational mode
and not in the configuration mode
|
root@SRX-A> set chassis cluster cluster-id 1 node 0 reboot
|
|
root@SRX-B> set chassis cluster cluster-id 1 node 1 reboot
|
After that the device will reboot and the
interface numbering will change.
Step 2 – set device specific configuration:
|
{primary:node0}
#DEVICE A host-name
set groups node0 system host-name SRX-A
#Device A's management IP address on fxp0 interface
set groups node0 interfaces fxp0 unit 0 family inet address
<ip address/mask>
#Device B's host name
set groups node1 system host-name SRX-B
#Device B's management IP address on fxp0 interface
set groups node1 interfaces fxp0 unit 0 family inet address
<ip address/mask
|
Step 3 – configure control and data links:
|
{primary:node0}
set interfaces fab0 fabric-options member-interfaces ge-0/0/2
set interfaces fab1 fabric-options member-interfaces ge-9/0/2
|
Note that
control link is configured automatically without any settings, the control and
data links are vary from each model.
Step 4 –
configure redundancy groups:
In my
case I will need 4 different redundancy groups:
Reth0
for the control plan – no interfaces are associated with this group.
Reth1
for LAN side connectivity using VLAN tagging.
Reth2
and Reth3 for each WAN link – hence 2x ISP BGP peer
|
set chassis cluster reth-count 4
set chassis cluster redundancy-group 0 node 0 priority 100
set chassis cluster redundancy-group 0 node 1 priority 1
set chassis cluster redundancy-group 1 node 0 priority 100
set chassis cluster redundancy-group 1 node 1 priority 1
set chassis cluster redundancy-group 1 interface-monitor
ge-2/0/20 weight 255
set chassis cluster redundancy-group 1 interface-monitor
ge-11/0/20 weight 255
set chassis cluster redundancy-group 2 node 0 priority 100
set chassis cluster redundancy-group 2 node 1 priority 1
set chassis cluster redundancy-group 3 interface-monitor
ge-2/0/0 weight 255
set chassis cluster redundancy-group 3 interface-monitor
ge-11/0/0 weight 255
set chassis cluster redundancy-group 3 node 0 priority 100
set chassis cluster redundancy-group 3 node 1 priority 1
set chassis cluster redundancy-group 3 interface-monitor
ge-2/0/3 weight 255
set chassis cluster redundancy-group 3 interface-monitor
ge-11/0/3 weight 255
|
Step 6 – configure interfaces:
|
set interfaces ge-2/0/0 gigether-options redundant-parent reth2
set interfaces ge-2/0/3 gigether-options redundant-parent reth3
set interfaces ge-2/0/20 gigether-options redundant-parent reth1
set interfaces ge-11/0/0 gigether-options redundant-parent reth2
set interfaces ge-11/0/3 gigether-options redundant-parent reth3
set interfaces ge-11/0/20 gigether-options redundant-parent
reth1
set interfaces fab0 fabric-options member-interfaces ge-0/0/2
set interfaces fab1 fabric-options member-interfaces ge-9/0/2
set interfaces reth1 vlan-tagging
set interfaces reth1 redundant-ether-options redundancy-group 1
set interfaces reth1 unit 100 description LAN
set interfaces reth1 unit 100 vlan-id 100
set interfaces reth1 unit 100 family inet address 192.168.100.1/24
set interfaces reth1 unit 101 description LAN
set interfaces reth1 unit 101 vlan-id 101
set interfaces reth1 unit 101 family inet address
192.168.101.1/24
set interfaces reth2 description EXTERNAL-PRIMARY
set interfaces reth2 redundant-ether-options redundancy-group 2
set interfaces reth2 unit 0 family inet address 1.1.1.1/29
set interfaces reth3 description EXTERNAL-SECONDARY
set interfaces reth3 redundant-ether-options redundancy-group 3
set interfaces reth3 unit 0 family inet address 2.2.2.1/29
|
Step 7 – set security parameters:
|
set security zones security-zone trust host-inbound-traffic
system-services all
set security zones security-zone trust host-inbound-traffic
protocols all
set security zones security-zone LAN interfaces reth1.100
set security zones security-zone LAN interfaces reth1.101
set security zones security-zone EXTERNAL host-inbound-traffic
system-services ssh
set security zones security-zone EXTERNAL host-inbound-traffic
system-services https
set security zones security-zone EXTERNAL host-inbound-traffic
protocols all
set security zones security-zone EXTERNAL interfaces reth3.0
set security zones security-zone EXTERNAL interfaces reth2.0
|
Step 8 – commit changes:
Few notes regarding Juniper SRX clustering:
When you activate clustering on Juniper SRX,
each node has its own data plan but only one control plan which is the active
member.
You can’t connect more then one device to each
node, in the same redundancy group, that’s because the node aggregate all
connected interfaces in this group.
So working with tringles in this setup simply
won’t work!
The only way to connect more then one link from
switch to the node is using link-aggregation (LACP, 802.3ad, etherchannel)
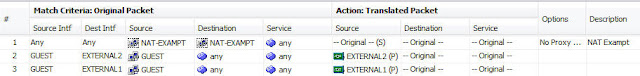
Also note redundancy group configuration which can be with VLAN tagging (as Cisco routers sub-interfaces with encapsulation) or as L3 interface.
Next posts will be on BGP, firewall filters and
security policies.