In
the following post I will demonstrate how to configure HPE Comware 7 switch for
TACACS AAA services with Aruba ClearPass policy manager and Microsoft Active
Directory.
Network Topology
|
Device/Host
|
Version
|
IP Address
|
VLAN ID
|
|
Aruba
ClearPass Policy Manager
|
6.6.5.93747
|
192.168.0.19
|
1
|
|
HPE
FlexNetwork 5510HI JH148A
|
5510hi-cmw710-system-r1308-US.bin
|
192.168.0.222
|
1
|
|
Microsoft
Windows Server
|
2012 R2
running AD/CA/DHCP/DNS services
|
192.168.0.22
|
1
|
|
Microsoft
Windows 7
|
Professional
running SecureCRT
|
192.168.0.16
|
1
|
Switch configuration
First configure hwtacacs scheme:
|
hwtacacs scheme CPPM
primary authentication 192.168.0.19
primary authorization 192.168.0.19
primary accounting 192.168.0.19
key authentication simple <PASSWORD>
key authorization simple <PASSWORD>
key accounting simple <PASSWORD>
user-name-format without-domain
nas-ip 192.168.0.222
#
|
Next configure domain:
|
domain mlab.local
authentication login hwtacacs-scheme CPPM
local
authorization login hwtacacs-scheme CPPM
local
accounting login hwtacacs-scheme CPPM
accounting command hwtacacs-scheme CPPM
authorization command hwtacacs-scheme CPPM
#
|
In the following domain configuration we
authenticate/authorize and account every login with the CPPM (ClearPass Policy
Manager) and also authorize and account every command (which are optional)
Configure the use for default domain:
|
domain default enable mlab.local
|
Configure default role:
|
role default-role enable
|
Last configure user interface access:
|
line vty 0 63
authentication-mode scheme
user-role network-operator
command authorization
command accounting
#
|
Aruba ClearPass Policy Manager Configuration
Launch the CPPM web interface and go to
Configuration -> Network -> Devices and click on Add.
Type in the device name, IP address, TACACS
shared secret (the same password as we configured in the switch configuration
under hwtacacs scheme) and choose H3C as vendor name:
Click Add to finish.
Next go to Administration -> Dictionaries
-> TACACS+ Services, check the shell dictionary and click Export:
An XML file will be saved, open it with text
editor (such Notepad++) and add the following two lines:
|
<ServiceAttribute
dataType="Unsigned32" dispName="Privilege level"
name="priv-lvl"/>
<ServiceAttribute
dataType="Unsigned32" dispName="Roles"
name="roles"/>
|
Shown here marked in yellow:
Next go to Configuration -> Identity ->
Roles and click Add.
As roles are only tags on CPPM add two roles –
one for network admin and the other for network operator:
Each role will have different privileges while
login into the switch.
Now go to Configuration -> Identity ->
Role Mappings and click Add,
In the following example I’m using the MLAB
active directory as authentication/authorization source and looking at the
department attribute (from the AD) to map a role, an account from the IT
department will receive MLAB Network-admin role while an account from the
helpdesk department will receive MLAB Network-operator role:
Note that the department attribute should be
enabled under the authentication source -> attributes.
Next go to Configuration -> Enforcement ->
Profiles and click Add
Under template select TACACS+ Based Enforcement
and type the profile name:
Click Next
Under Services, select Privilege 15, add Shell
for Selected Services and add two following two Service Attributes:
Click Next
Check Enable to permit unmatched commands:
Here we can select the commands that we permit
or deny, for the following profile, by clicking Add and type in the required
commands.
Click Finish
Repeat this step for the network operator
enforcement profile but this time set the privilege level to 1 and role to
network-operator:
Next go to Configuration -> Enforcement ->
Policies and click Add,
Type in the Enforcement policy name, select
TACACS+ as Enforcement Type and select TACACS Deny Profile as Default Profile:
Click Next
Under Roles click Add Rule, select Type=Tips,
Name=Role, Operator=EQUALS and Value=MLAB Network-admin. Select Enforcement
Profile Comware7_Network-Admin:
Add one more rule for network-operator:
Click Finish
Last we need to configure the TACACS service,
go to Configuration -> Services and click Add, Choose TACACS+ Enforcement, type in the service
name, check Authorization and add service rules as required, here in this
example I used TACACS protocol as match for this service:
Click Next
Under Authentication select the authentication
source, in this example I choose the AD:
Click Next
Under Authorization select the authorization
source, again here I choose the AD:
Click Next
Under Roles choose the role mapping [MLAB
TACACS Role mapping]:
Click Next
Under Enforcement choose the enforcement policy
[MLAB TACACS Enforcement]:
Click Next
In the Summary tab click Finish.
Go to Configuration -> Services and reorder
the services in order that TACACS service will be first:
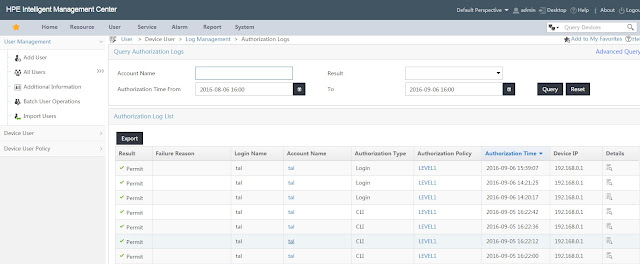
Verification and information
Under Monitoring -> Live Monitoring -> Access
Tracker we can see the authentication and authorization commands:
Under Monitoring -> Live Monitoring ->
Accounting we can see the start/stop session time and the command that issued
by each user:
Next post i will explain how to configure Wired 802.1x policy along with web health check and MAC authentication.