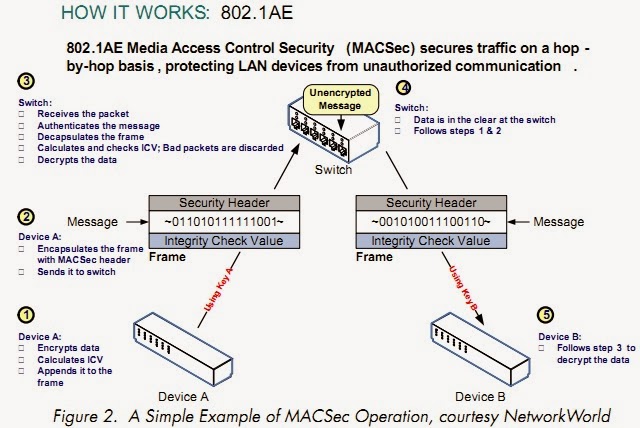
For that purpose we have got the MACSec or 802.3ae protocol.
here is some technical information which i gathered:
MacSec - 802.1ae is the IEEE MAC Security standard (also known as MacSec) which defines connectionless
data confidentiality and integrity for media access independent protocols.
Security Association Protocol (SAP)
negotiation—When both sides of a link support encryption, the supplicant
and the authenticator negotiate the necessary parameters to establish a
security association (SA).
Link Security
When both sides of a link support
802.1AE Media Access Control Security (MACsec), a SAP negotiation is performed.
An EAPOL-Key exchange occurs between the supplicant and the authenticator to
negotiate a cipher suite, exchange security parameters, and manage keys.
Successful completion of all three tasks results in the establishment of a
security association (SA).
Depending on your
software version, crypto licensing, and link hardware support, SAP negotiation
can use one of the following modes of operation:
And now for the practical section - for using MACSec you will have to use a switch with supported hardware such as 3560-X, 3750-X, 4500-6500 series or even Nexus (the complete list can be found on Cisco site),here in my lab i used 3750-X.
Note that there is no need for C3KX-SM-10G module else you want to encrypt 10G links or one of the SFP ports! For MACSec you can use any one of the copper ports in the switch.
Then there is the IOS issue - you have to use 15.x or newer.
Here is the lab setup:
And the configuration:
3750X-A:
|
interface
GigabitEthernet1/0/1
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 1-10
switchport mode trunk
switchport nonegotiate
load-interval 30
cts manual
no propagate sgt
sap pmk 12345ABCDE mode-list gcm-encrypt
end
|
3750X-B:
|
interface
GigabitEthernet1/0/1
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 1-10
switchport mode trunk
switchport nonegotiate
load-interval 30
cts manual
no propagate sgt
sap pmk 12345ABCDE mode-list gcm-encrypt
end
|
Note that this configuration is using manual CTS with pre-shared key (12345ABCDE), there is also an option to use certificates and authentication with RADIUS server but this is out of the scope for this post.
Let's verify connectivity:
|
3750X-B#show
cts interface gigabitEthernet 1/0/1
Global
Dot1x feature is Disabled
Interface
GigabitEthernet1/0/1:
CTS is enabled, mode: MANUAL
IFC state: OPEN
Authentication Status: NOT APPLICABLE
Peer identity: "unknown"
Peer's advertised capabilities:
"sap"
Authorization Status: NOT APPLICABLE
SAP Status:
SUCCEEDED
Version: 2
Configured pairwise ciphers:
gcm-encrypt
Replay protection: enabled
Replay protection mode: STRICT
Selected cipher: gcm-encrypt
Propagate SGT: Disabled
Cache Info:
Cache applied to link : NONE
Statistics:
authc success: 0
authc reject: 0
authc failure: 0
authc no response: 0
authc logoff: 0
sap success: 4
sap fail: 0
authz success: 0
authz fail: 0
port auth fail: 0
L3 IPM:
disabled.
|
|
3750X-B#show
cts macsec counters interface gigabitEthernet 1/0/1
CTS
Security Statistic Counters:
rxL2UntaggedPkts = 0
rxL2NotagPkts = 196
rxL2SCMissPkts = 0
rxL2CTRLPkts = 0
rxL3CTRLPkts = 0
rxL3UnknownSAPkts = 0
rxL2BadTagPkts = 0
txL2UntaggedPkts = 0
txL2CtrlPkts = 0
txL3CtrlPkts = 0
txL3UnknownSA = 0
SA Index : 1
rxL2ReplayfailPkts = 0
rxL2AuthfailPkts = 0
rxL2PktsOK = 716
rxL3AuthCheckFail = 0
rxL3ReplayCheckFail = 0
rxL2SAMissPkts = 196
rxL3EspGcm_Pkts = 0
rxL3InverseCheckfail = 0
txL3Protected = 0
txL2Protected = 1677
GENERIC
Counters:
CRCAlignErrors = 0
UndersizedPkts = 0
OversizedPkts = 0
FragmentPkts = 0
Jabbers = 0
Collisions = 0
InErrors = 0
OutErrors = 0
ifInDiscards = 0
ifInUnknownProtos = 0
ifOutDiscards = 0
dot1dDelayExceededDiscards = 0
txCRC = 0
linkChange = 0
|
|
3750X-B#show
macsec interface gigabitEthernet 1/0/1
MACsec is enabled
Replay protect : enabled
Replay window : 0
Include SCI : yes
Cipher : GCM-AES-128
Confidentiality Offset : 0
Capabilities
Max. Rx SA : 16
Max. Tx SA : 16
Validate Frames : strict
PN threshold notification support : Yes
Ciphers supported : GCM-AES-128
Transmit Secure Channels
SCI : 708105E91E810000
Elapsed time : 01:01:00
Current AN: 1 Previous AN: 0
SC Statistics
Auth-only (0 / 0)
Encrypt (20704 / 0)
Receive Secure Channels
SCI : D48CB56FB1010000
Elapsed time : 01:01:00
Current AN: 1 Previous AN: 0
SC Statistics
Notvalid pkts 0 Invalid pkts 0
Valid pkts 15330 Late pkts 0
Uncheck pkts 0 Delay pkts 0
Port Statistics
Ingress untag pkts 0
Ingress notag pkts 219
Ingress badtag pkts 0 Ingress unknownSCI pkts 0
Ingress noSCI pkts 0 Unused pkts 0
Notusing pkts 0 Decrypt bytes 30119536
Ingress miss pkts 219
|
|
3750X-B#
show macsec summary
Interface Transmit SC Receive SC
GigabitEthernet1/0/1 1 1
|
Final note:
Basically MACSec should work without intermediate devices on the link, but i have tested it on several links including Metro-Ethernet and Carrier Ethernet and it works fine.
If for some reason you have problems raising MACSec on these kind of links please check the provider settings it's probably there (no CDP neighbors and STP problems are good indication that the provider settings are wrong!)