This post will demonstrate, step by step, how to configure
a site-to-site VPN between 2 Check Point security gateways, were all traffic from
site B is routed through site A, and will use site A public IP for internet
access – hence full tunnel from site B to site A.
Each site is managed by its own, so I have two security
management servers.
This is the network topology diagram:
First step we will create network objects:
Right click on Networks -> Network and add the remote
site network
Now create a simple group which will gather all remote site
networks, in case we have more than one, right click on Groups -> Groups
-> Simple group
In the following group we will add all the remote networks.
Repeat these steps for local networks and group:
Now let’s create the remote peer object, right click on
Check Point -> Check Point -> More -> Externally Managed VPN Gateway
Type in the machine name, IP address and check Firewall and
IPSec VPN checkboxes:
Next choose Topology, in the right pane, and under VPN
Domain choose Manually defined and select the remote peer group we made
earlier:
Do the same step for our locally security gateway, and make
sure that the local VPN group is set:
This group represent the local networks which are behind our
security gateway.
Next let’s create the VPN community, select IPSec VPN in the
products pane, click on New and choose Star Community:
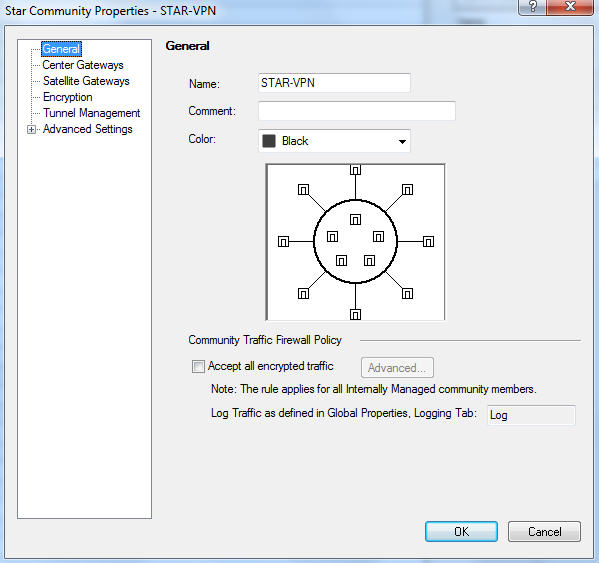
Type a name for the community and check Accept all encrypted
traffic check box:
Select Center Gateways in the right pane, click Add and
choose the gateway that will be the center, in our case CP-CLUSTER, which is
the security gateway of site A:
Then select Satellite Gateways, click Add and choose site B
gateway, in our case CP-SG3:
Leave encryption with his default settings:
Select Tunnel Management, check Set Permanent Tunnels check box:
Select Advanced Settings -> VPN Routing and click on To
Center, or through the center to other satellites, to internet and other VPN
targets:
This setting will force the satellites to route all traffic
through the center gateway.
Select Excluded Services, click Add and choose IKE:
Select Shared Secret, check Use Only Shared Secret for all
External members, then click on the peer name, click edit and type in the
shared secret (Check Point recommend to use a shared secret with no less the 20
characters):
Select Advanced VPN Properties, and under NAT check Disable
NAT inside the VPN community:
Click OK and close the Star Community.
Last step we need to create Firewall policy to allow traffic
between the two sites, select Firewall in the products pane and choose Policy.
Add new rule between the two groups (local and remote VPN groups) in both
directions:
To finish click on Install Policy.
Please note that those steps should be configured on both
sides each with his corresponding objects and settings.
Also the following steps should be configured only on the center
gateway -
Add Firewall policy rule to allow site B networks to access
the internet:
And add NAT rule for remote site network:
Now when client in network 192.168.20.0/24 will access the
internet, he will pass-through CP-CLUSTER and will use his external IP.
Products List:
CP-CLUSTER – Check Point R77.20
CP-SG3 – Check Point R77.30